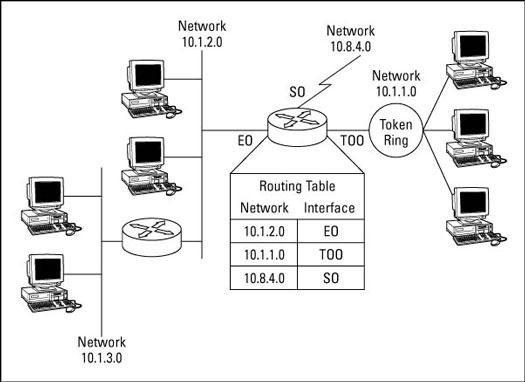
Macintosh computers have been at the forefront of wireless networking with AirPort, Apple's name for the Wi-Fi technology used in modern Macs. Most new Macs have AirPort Extreme — a newer, faster version of AirPort — built right in. If you buy a new Mac without AirPort Extreme you may be able to install a card. By using AirPort or AirPort Extreme, you can connect your Mac to any 802.11b/g Wi-Fi network.
 | Some Macs —such as the Mac mini — can only be upgraded by an Apple repair professional. When you buy a new Mac, spend a little extra money to get an AirPort Extreme card preinstalled — it's worth it. |
Installing an AirPort card in an iBook
Follow these steps to install an AirPort card in an iBook:
1. Shut down your iBook and remove the battery.
To remove the battery, use a coin to turn the lock screw on the bottom of the iBook to the unlocked position.
2. On the front of your iBook, push the keyboard release tabs (see Figure 1) towards the front of the iBook and gently lift the keyboard out of the chassis. You don't need to disconnect the keyboard; simply rest it upside down on the touch pad.
Figure 1: The keyboard release tabs.3. Locate the built-in AirPort antenna in the space provided for the AirPort card.
If you don't see a space for the AirPort card, your iBook either is not compatible with AirPort or it already has AirPort installed.
4. Connect the antenna to the antenna port on the AirPort card.
5. Insert the AirPort card into the slot, ensuring that the connector pins seat firmly in the AirPort card socket.
 | Do not force the card into position. If the AirPort card and the port on your computer don't match, you probably have the wrong kind of card for your iBook model. |
6. Seat the AirPort card wire retention clasp and replace the keyboard and battery.
Installing an AirPort card in an eMac
Follow these steps to install an AirPort card in an eMac:
1. Open the DVD-ROM disc tray and leave it open.
2. Shut down your computer and make sure that the power is off.
 | Disconnect the power cable to make sure that the computer doesn't accidentally turn on while you are installing the card. |
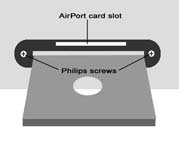
3. Remove the two Philips-head screws on the cover inside the disc tray to reveal the AirPort card slot (see Figure 2).
Figure 2: The AirPort card slot.4. Disconnect the antenna from the cover and then press the antenna into the AirPort card's antenna port.
5. Insert the AirPort card firmly into the slot until it seats and then reinstall the cover inside the disc tray.
Connecting to a Wi-Fi access point
To connect to a Wi-Fi access point, follow these steps:
1. If AirPort isn't already enabled, click the AirPort icon on the menu bar in the upper-right corner of the screen and choose Turn AirPort On.
2. Click the AirPort icon in the menu bar again and choose Other to connect to a new Wi-Fi network.
 | If the access point is set to broadcast its SSID, it may appear in the list of available networks in the AirPort menu. If you see the network to which you want to connect listed, click its name. |
3. In the resulting Closed Network dialog box, enter the network's SSID in the Network Name text box.
4. Choose a Wireless Security method as needed for the network.
5. Click OK to connect to the network.
6. Check the status and signal strength of the Wi-Fi network by clicking the AirPort icon in the menu bar and choosing Open Internet Connect.
Managing Wi-Fi networks
Follow these steps to manage your Wi-Fi network:
1. Choose Apple --> System Preferences to open the System Preferences window.
2. Click the Network icon to open the Network dialog box.
3. Choose AirPort in the Show menu to reveal AirPort settings.
4. In the By Default, Join menu, choose Preferred Networks.
5. In the resulting list, rearrange the order by clicking and dragging networks up or down in the list.
6. To remove a network from the list, click the network to select it and then click the Remove (-) button.
7. Select a network and choose Edit to change encryption keys and other network details for a given network.
8. When you are done making changes, click the Apply Now button and then quit System Preferences.
 | To update the AirPort software, choose Apple --> Software Update to run the Software Update. Download and install any necessary updates to your computer.
|