Installing and configuring TCP/IP creates most of the files you need automatically. Just point your mouse, click, and type some text. Your setup program creates and maintains the files for you.
The one exception is when you're working on an older UNIX computer or a very small Linux system that has no network setup program. In this sad case, the network administrator (who is probably you if you're reading this article) must create some files and edit others. How you do this is up to you. A text editor works just fine.
The hosts file
You start with the most fundamental file that you need for communicating with other computers on your network — the hosts file.
When you access another host by name on the Internet or any intranet/internet, your computer needs to know the remote host's IP address. You can get remote host addresses from DNS (Domain Name System) or from your computer's hosts file. This file lists the names and addresses of other hosts known by your computer.
When you need to know about thousands of hosts on the Internet, maintaining the hosts file is really too cumbersome a mechanism. Imagine having to spend all that time updating it as computers come and go or relocate on the Internet! In that case, you need DNS to locate remote hosts.
The location and name of the hosts file depend on the operating system and version of TCP/IP you use. Table 1 lists the hosts file locations for a few implementations of TCP/IP.
Table 1: Popular Locations for Hosts Files
Location | Operating System | Vendor |
/etc/hosts | Linux and UNIX | Various |
c:\winnt\system32\drivers\etc\hosts | Windows NT, 2000 | Microsoft |
c:\windows\hosts | Windows 95, 98 | Microsoft |
c:\windows\system32\drivers\etc\hosts | Windows XP | Microsoft |
Netinfo database | Apple | Mac OS X |
/etc/hosts | zOS | IBM |
 | Maintaining the hosts file |
Your operating system or TCP/IP product provides a hosts file to get you started. You, the network administrator, the system manager, or whoever is in charge of network configuration, maintains the hosts file. As you add host names and addresses, you need to update the file. If your vendor did not include a network configuration tool, you get to use a plain old text editor, such as Notepad, to type in two columns of information — column 1 for the host's IP addresses and column 2 for its names.
Finding what's in the hosts file
Figure 1 shows the contents of a hosts files taken from a computer running UNIX. Looking at Figure 1, you may think there are several host names on a line. But the first name is the host name and the following name(s) are nifty host name aliases. Look carefully at the entry for the host spiderman. Do you see an alias, peterparker? You can refer to the computer as either spiderman or peterparker. Anything preceded by a # character is a free-form comment about things such as the computer's owner, location, operating system, and whatever else you think is meaningful.
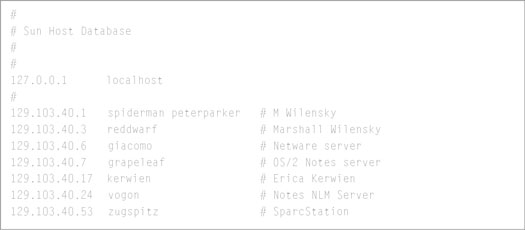
Figure 1: This hosts file, created with a text editor, contains the IP addresses and the host names.
Improving TCP/IP's digestion of the hosts file
 | Without an up-to-date hosts file, you may not be able to find other computers on the network, so it's important to update the file whenever a computer changes its name or address or joins or leaves the network. Listing the computers in most frequently used order is a good idea. TCP/IP searches the hosts file sequentially from top to bottom until it finds the computer it's looking for, so if you have a large hosts file, ordering the computers appropriately gives you a performance advantage. |
The trusted hosts file
On Linux and UNIX operating systems, the file /etc/hosts.equiv lists the other hosts on the network that your computer trusts; this is your trusted hosts file. This file is easy to create with any text editor. It has only one column — the host name of each computer you trust. (See Figure 2.)

Figure 2: The hosts.equiv file lists trusted hosts.
 | Be very careful with the hosts.equiv file. Any remote computer listed here is a trusted host, and all of its users can log on to your computer without knowing a password. |
Some operating systems implement trust by using other methods besides a trusted hosts file. Microsoft Windows NT and 2000 Server, for example, don't use the hosts.equiv file. Instead, you set up trust relationships when you set up security policies for your computer or Active Directory for your domain. Trust relationships are between domains as opposed to individual hosts. See Figure 3.
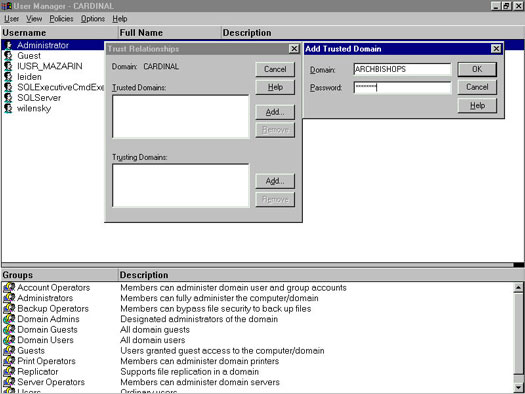
Figure 3: The entire cardinal domain (Windows NT Server 4.0) trusts the entire Archbishops domain.
The trusted hosts print file
On Linux and UNIX, you can use the /etc/hosts.lpd file to list the remote hosts that can print on the printer attached to your computer. The simplest hosts.lpd file possible contains just one asterisk (*) character, which means that any host on the network can share your printer. If you don't have a hosts.lpd file, it's the same as having the file with an asterisk in it. So if you aren't prepared to be super generous with your printer, you'd better create one of these hosts.lpd files. Any text editor will do.
 | Speaking of generosity, how generous can you afford to be with your printer? If you share your printer with all of the hosts on your network, will the volume of remote print jobs mean that you always have to wait before you can print your own stuff? Will this same print job traffic clog up the network connection media (the cables)? You should ask yourself these questions before editing your hosts.lpd file. |
No comments:
Post a Comment