If you know the MAC address for an unauthorized user who is accessing your network, you can block the user from your network's router or use a security program to restrict access. Although blocking an intruder using an Internet security program installed on a specific computer does protect the data on that computer, it does not block the intruder from the rest of your network.
Blocking a user from the router
Use the following steps to block a user from your network's router:
1. Log in to the control panel for your WAP (Wireless Access Point) using a Web browser.
2. Locate the filter controls and select MAC filters (see Figure 1).
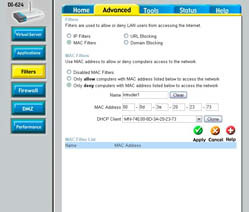
Figure 1: Filter unauthorized MAC addresses from your network.
3. Select the Only Deny Computers option to create a MAC filter that will deny access to a specific MAC address.
4. Enter a name for the rule, and enter the MAC address for the unwanted device.
5. Click OK or Apply to save your changes. The new MAC filter appears in your list of MAC filters, as shown in Figure 2.
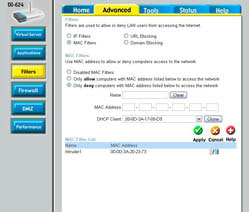
Figure 2: The MAC filter now appears in your list of filters.
6. Double-check that SSID broadcast is disabled in your access point.
 | Disable SSID broadcast before you change the SSID and other network security keys as described in the following step. |
7. Change the SSID, WEP key, WPA-PSK passphrase, and administrator password for your access point.
 | You should change the SSID and all security keys in your wireless devices any time you even suspect that your network has had an unauthorized intrusion. Although MAC filtering creates a roadblock for the intruder, diligent intruders can get around that roadblock either by MAC address spoofing, or by simply using a different computer. |
Blocking a user with a security program
Follow these steps to use a security program to block a user:
1. Open your Internet security program, open the Wi-Fi detection screen used for detecting computers on your network, and find local computers.
2. Select the computer you want to restrict and click Properties.
3. Block access from the offending computer. In Trend Micro's Internet security program, click the Add Exception button to block the computer.
Have any queries feel free to mail me
david.singh@verizon.net
No comments:
Post a Comment